Install Waydroid
paru -Sy wadroid
Initialize waydroid and allow it to download the latest Lineage OS SDK + GAPPS (Google services)
waydroid init -s GAPPS
sudo systemctl enable --now waydroid-container
Install waydroid-extras
https://github.com/casualsnek/waydroid_script
paru -Sy waydroid-script-git
Activate google services in Waydroid
Start waydroid as any desktop application
waydroid-extras google
Copy the returned numeric ID, then open "https://google.com/android/uncertified/?pli=1". Enter the ID and register it. Wait 10-20 minutes for device to get registered. Then clear Google Play Service's cache and try logging in!
Install Magisk Delta (Kitsune Mask)
sudo waydroid-extras install magisk
Once the device reboots enable zygisk in magisk settings

Libndk
Libndk is a translation layer for arm apks (since this is a 64 bit device) We can install it using the below command
sudo waydroid-extras install libndk
Magisk modules
magisk-frida Used to start the latest Frida server automatically on boot, though you might prefer magisk-strongR-frida, which is a fork that uses an alternative Frida version to avoid detections (can be found here)
MagiskTrustUserCerts Used to trust all user certificates
For sslpining we will use LSPosed_mod (Download the Zygisk version, since we enabled Zygisk a moment ago)
Download all the modules and push them to Downloads
adb push MagiskFrida-*.zip /sdcard/Download
adb push AlwaysTrustUserCerts.zip /sdcard/Download
adb push LSPosed-*-zygisk-release.zip /sdcard/Download
Install all of them in Magisk
Reboot the device with (Don't use the reboot button in Magisk)
sudo systemctl restart waydroid-container
Check if the LSPosed app is installed in the app drawer, if not install it manually by extracting the apk from the zip and installing it with
unzip LSPosed-*-zygisk-release.zip -d LSPosed
waydroid app install LSPosed/manager.apk
Verify that LSPosed is activated

Setting up Burp as proxy and SSL pinning bypass
The LSPosed module I will be using is unfortunately quite old JustTrustMe. Basically it still receives some maintenance but there is no release since 2016! Hence we will have to build it ourselves or use this fork
git clone https://github.com/Fuzion24/JustTrustMe
cd JustTrustMe
./gradlew assembleRelease
./gradlew installRelease
Verify that the module is installed and enable it

Start Burp and set it to listen to all interfaces
 Verify that it can be reached through the android device by visiting the waydroid tun interface
Verify that it can be reached through the android device by visiting the waydroid tun interface
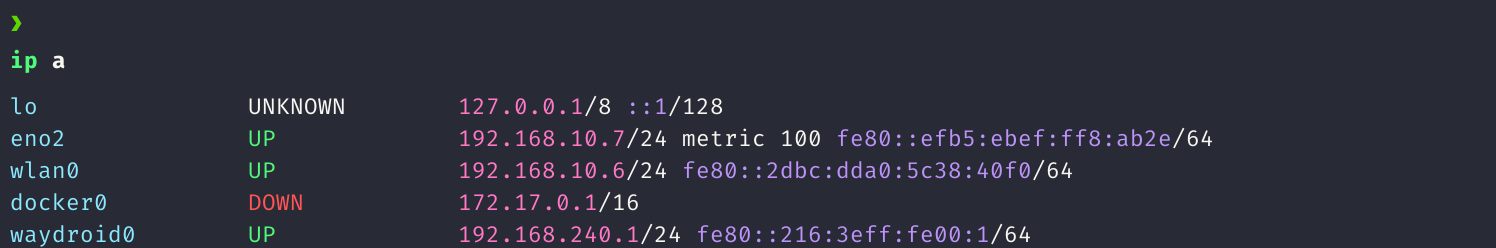
Our target interface is waydroid0
Thus IP: 192.168.240.1 in the above example, lets verify that it can be reached from a browser(I recommend installing Kiwi browser instead of the default btw) in the android device. Remember to use your burp port
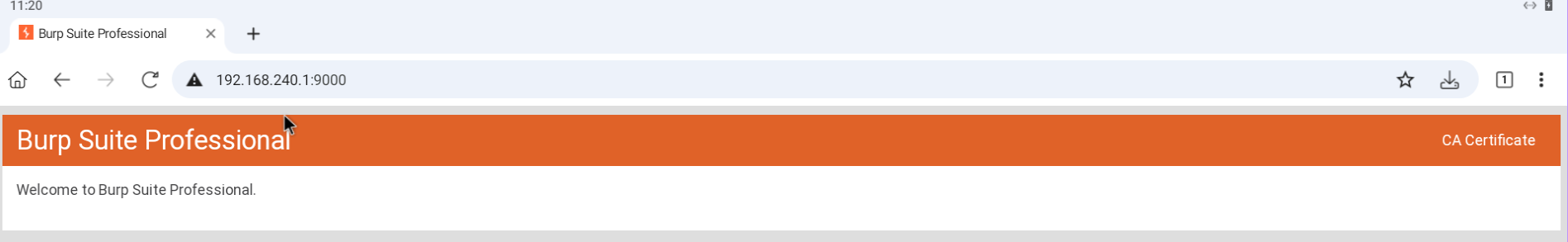 If you see the
If you see the Welcome page then you are good to go
Thus using adb we will now tell the android device to use burp as a proxy by proxying all traffic through that interface
Before we do that lets install our burp certificate on the device
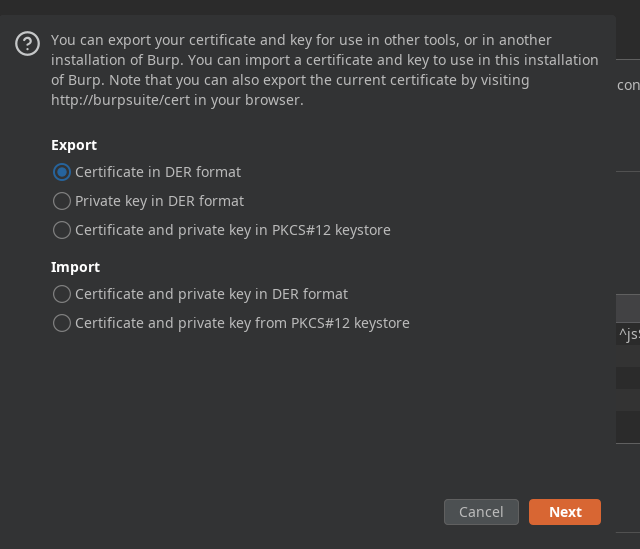 Export the certificate and convert the certificate to
Export the certificate and convert the certificate to pem format
openssl x509 -inform DER -in cert.der -out cert.pem
Push it to the device
adb push cert.pem /sdcard/Download
Go to settings -> Encryption & Credentials -> Install a certificate -> CA Certificate -> Install anyway and select the cert.pem file
Normally this method wouldn't work for all apps, but since we installed AlwaysTrustUserCerts module, all certificates are now trusted as if they were system certificates
Reboot the device with
sudo systemctl restart waydroid-container
Now let's tell our device to use the proxy we have setup. Most people here use some way to configure android's proxy settings and set burp suite as a system-wide proxy. I avoid that since if an app developer chooses to make a request with the NO_PROXY flag, it will bypass the proxy. Instead I use the following VPN app rethink-app and configure it like below:
-
Click on configure
-
Set up burp as the proxy
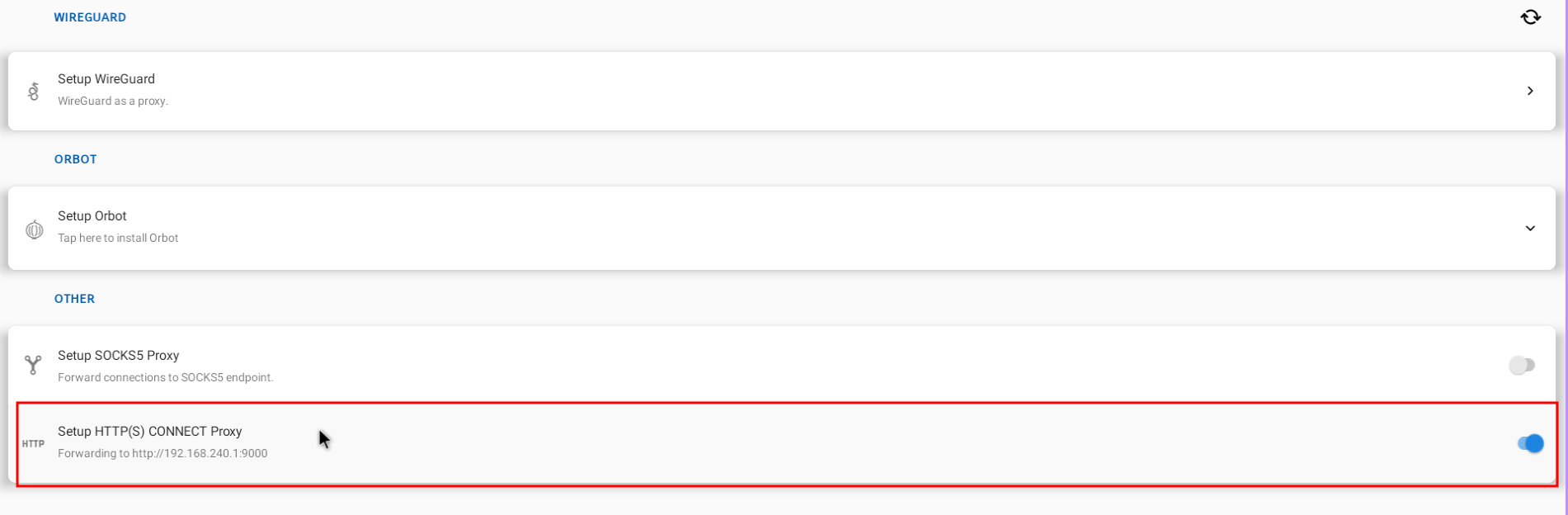
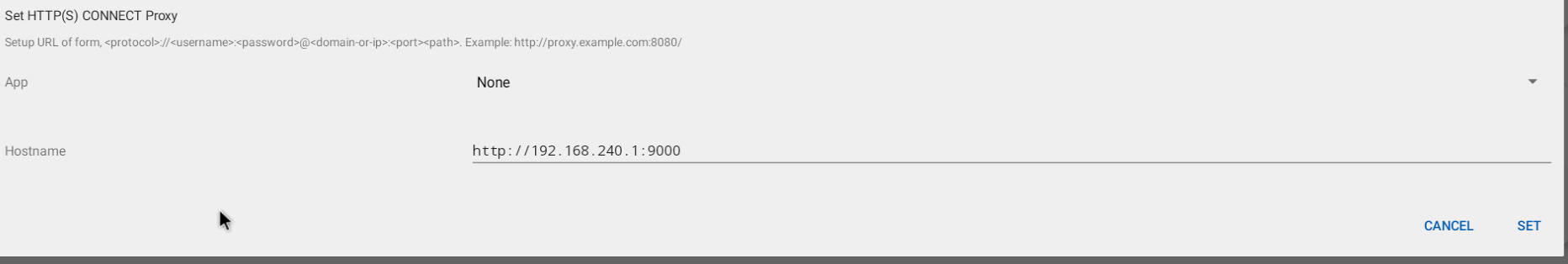
-
Don't rout private IPs through the proxy, since this will break adb connections!
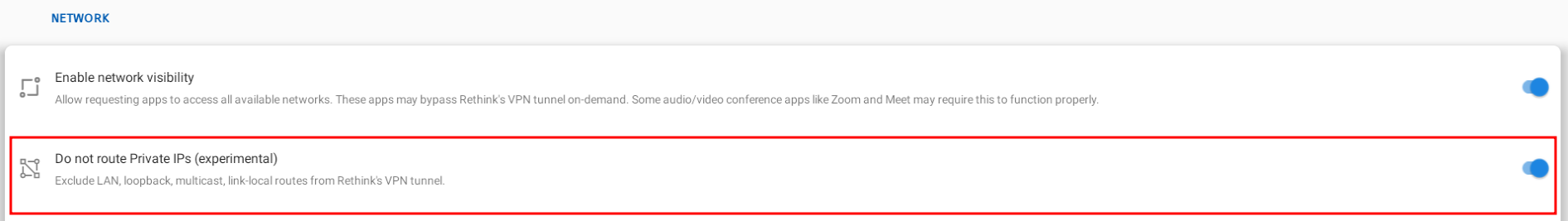
-
Configure DNS servers to be the default
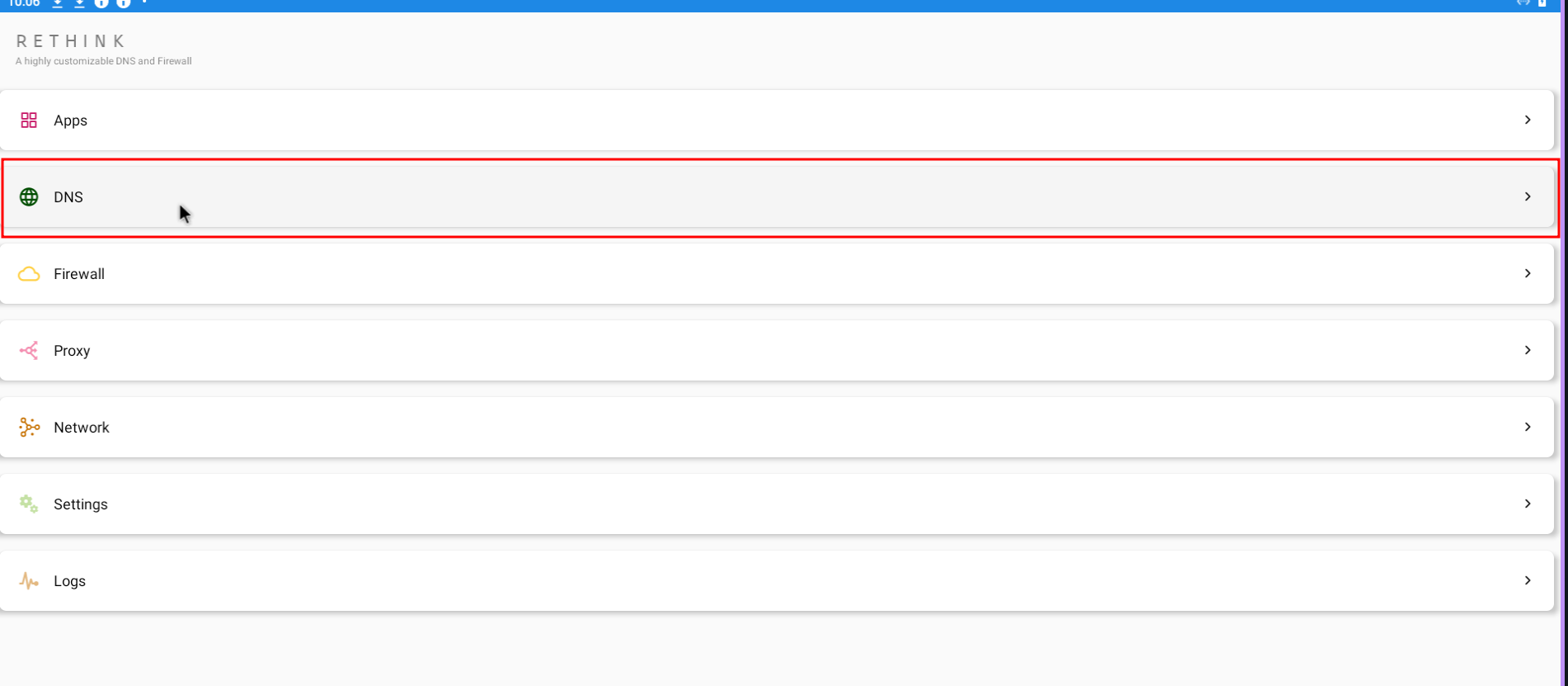
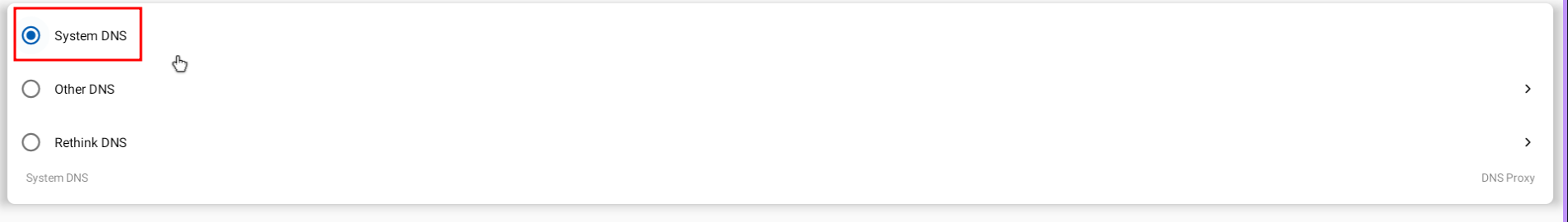
Wooohoo! Now you can intercept all traffic from your android device